Usually we use a external RADIUS server(ACS or ISE) for authentication in big enterprise but in small office it’s not feasible solution because of cost.
In this kind of situation, a standalone/autonomous AP can act as a RADIUS server. User are authenticate against the Local database configured in AP.
Autonomous AP can authenticate using LEAP, EAP-FAST and MAC based authentication.
In this post we will see, how to configure LEAP and local RADIUS server on AP.
To configure LOCAL RADIUS server on AP:
- IOS on AP must have at least 12.2(11)JA or higher version
- Remember LEAP is not strong method for authentication
Via CLI:
Switch config for AP connection:
int fa 0/15
switchport mode trunk
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 100, 101
Step1: Configure the SSID and map to a VLAN
Config t
Dot11 ssid data1
Vlan 101
Authentication open eap local_eap
Authentication network-eap local_eap
Authentication key-management wpa version 1
Guest-mode
end
Step2: Configure the radio and Ethernet interface
Config t
Interface dot11Radio0
ssid data1
exit
!
Interface dot11Radio0.100
encapsulation dot1Q 100
!
Interface dot11Radio0.101
encapsulation dot1Q 101
bridge-group 101
exit
!
int fa 0.100
encapsulation dot1Q 100
!
int fa0.101
encapsulation dot1Q 101
bridge-group 101
exit
Step3: Assign encryption to SSIDs with VLAN
Int dot11Radio0 Encryption vlan 101 mode ciphers tkip
Step4: Configure AP for management
Int BVI1 Ip address 10.35.100.250 255.255.255.0 ! Ip default-gateway 10.35.100.254
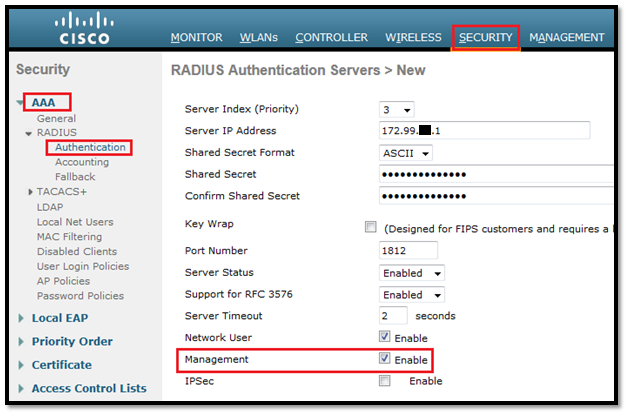
Step5: Define a AAA group, AAA login method and configure RADIUS server with its own IP address
aaa new-model ->This command reinitializes the authentication, authorization and accounting functions. aaa group server radius radius_leap server 10.35.100.250 auth-port 1812 acct-port 1813 ->A server group for RADIUS is created called "rad_leap" that uses the server at 10.35.100.250 on ports 1812 and 1813. aaa authentication login local_eap group radius_leap -> Authentication [user validation] is to be done for users in a group called "local_eap" who use server group "radius_leap". aaa authentication exec default local
Step6: Configure local AP as authenticator
radius-server host 10.35.100.250 auth-port 1812 acct-port 1813 key leap12345
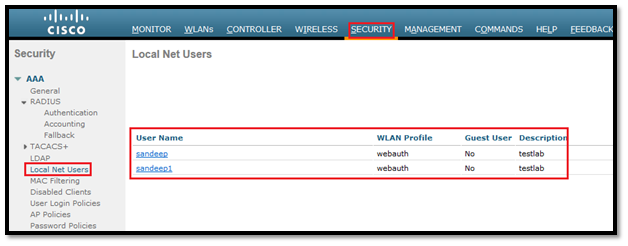
Step7: Configure local users to authenticate as NAS entries.
Radius server local Nas 10.35.100.250 key leap12345 User Sandeep password test12345 User Sandeep1 password rscciew123
Step8: Verification with screenshot
ap#sh dot11 associations
802.11 Client Stations on Dot11Radio0:
SSID [data1] :
MAC Address IP address Device Name Parent State
bd7b.a1d1.c289 10.35.101.252 ccx-client ap self EAP-Assoc
ap#sh dot11 associations ac7b.a1d1.c289 Address : bd7b.a1d1.c289 Name : ap IP Address : 10.35.101.252 Interface : Dot11Radio 0 Device : ccx-client Software Version : NONE CCX Version : 4 Client MFP : Off State : EAP-Assoc Parent : self SSID : data1 VLAN : 81 Hops to Infra : 1 Association Id : 1 Clients Associated: 0 Repeaters associated: 0 Tunnel Address : 0.0.0.0 Key Mgmt type : WPA Encryption : TKIP Current Rate : 54.0 Capability : WMM ShortHdr ShortSlot Supported Rates : 1.0 2.0 5.5 11.0 6.0 9.0 12.0 18.0 24.0 36.0 48.0 54.0 Voice Rates : disabled Bandwidth : 20 MHz Signal Strength : -37 dBm Connected for : 213 seconds Signal to Noise : 58 dB Activity Timeout : 50 seconds Power-save : Off Last Activity : 0 seconds ago Apsd DE AC(s) : BK BE VI VO Packets Input : 910 Packets Output : 175 Bytes Input : 130156 Bytes Output : 69771 Duplicates Rcvd : 0 Data Retries : 35 Decrypt Failed : 0 RTS Retries : 12 MIC Failed : 0 MIC Missing : 0 Packets Redirected: 0 Redirect Filtered: 0 Session timeout : 0 seconds Reauthenticate in : never