In this post we will learn how to use Auto Anchoring feature.
In simple words, Auto-anchoring is when we anchor a WLAN to a particular controller in the mobility domain or group.
It can be used for load balancing & Security. We can force clients to be on a particular controller regardless of the controller they access the wireless network from.
**The most common example/use for auto-anchor is with guest networking.
Let’s go into detail:
With auto-anchor, regardless of which controller’s APs a client associates with, the client traffic is anchored to this one controller. Auto-anchoring is basically symmetric tunneling using a fixed anchor. When a client first associates with a controller on an anchored WLAN, a Local Session entry is created for the client. The controller sends out a Mobile Announce message to the mobility group.
When that message is not answered, the foreign controller contacts the configured anchor controller and creates a foreign session for the client in its database. The anchor controller then creates an Anchor session for the client.
All traffic to and from the client associated with an anchored WLAN passes through the anchor controller. This is known as a bidirectional tunnel because the foreign controller encapsulates the client packets in EtherOverIP and sends them to the anchor. The anchor de-encapsulates the packets and delivers them to the wired network. Packets destined for the client are encapsulated in the EtherOverIP tunnel by the anchor and sent to the foreign controller. The foreign controller de-encapsulates the packets and forwards them to the client.
Guideline before Auto-Anchor configuration:
- We must add controllers to the mobility group member list before we can designate them as mobility anchors for a WLAN. How to Add, Check this post: Mobility Configuration on WLC
- We can configure multiple controllers as mobility anchors for a WLAN.
- We must disable the WLAN before configuring mobility anchors for it.
- Auto-anchor mobility supports web authorization but does not support other Layer 3 security types.
- We must configure the WLANs on both the foreign controller and the anchor controller with mobility anchors. On the anchor controller, configure the anchor controller itself as a mobility anchor. On the foreign controller, configure the anchor as a mobility anchor.
- Auto-anchor mobility is not supported for use with DHCP option 82.
- When using the mobility failover features with a firewall, make sure that the following ports are open:
- UDP 16666 for tunnel control traffic
- IP Protocol 97 for user data traffic
- To check the connectivity and peer kee-palive timers, use these CLI commands :
- mping peer-ip-address – used to test the Control Path between mobility peers
- eping peer-ip-address – used to test the Data Path between mobility peers
- show mobility summary – used to view mobility configuration and timers
How to configure Auto-anchoring
Our main aim is to force clients to be on a particular controller regardless of the controller they access the wireless network from. As per my Topology client connects to AP001 which is connected to WLC2 and traffic is tunneled back to WLC1, client must get IP from VLAN 192.

WLC2 (Foreign) Configuration:
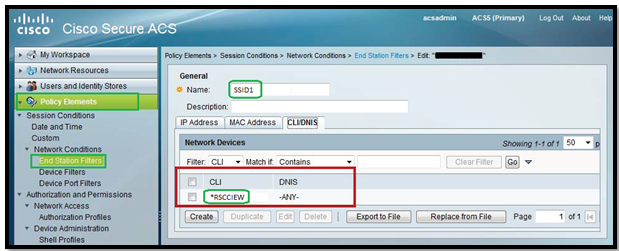
Step1: Create a WLAN (In my example: RSCCIEW)
Step2: Assign to Management interface and choose the security to webauth.

Step3: Add WLC1 to its mobility list

Step4: Go to WLAN tab and assign the ANCHOR WLC.

In this case we assign the ANCHOR WLC to WLC1:

WLC1 (ANCHOR) Configuration:
Step1: Create the same WLAN as we did for WLC2 (Foreign)
Step2: Assign the interface (guest), except this everything should be same as WLC2.

Step3: Add WLC2 to its mobility list

Step4: Go to WLAN tab and assign the ANCHOR WLC.

In this case we will assign the ANCHOW WLC IP to local.

That’s all about configuration, Lets jump for verification:
From WLC2 (Foreign WLC)

From WLC1 (ANCHOR WLC) before webauth authentication.

Now create a Local net user for testing

From WLC1 (ANCHOR WLC) After webauth authentication.

Here are the complete logs from WLC1 CLI:
(WLC1) >debug client 54:26:96:3e:4b:ee
(WLC1) >*mmListen: Nov 07 10:05:04.763: 54:26:96:3e:4b:ee Adding mobile on Remote AP 00:00:00:00:00:00(0)
*mmListen: Nov 07 10:05:04.763: 54:26:96:3e:4b:ee override for default ap group, marking intgrp NULL
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee Applying Interface policy on Mobile, role Unassociated. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 0
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee Re-applying interface policy for client
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee 0.0.0.0 START (0) Changing IPv4 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2219)
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee 0.0.0.0 START (0) Changing IPv6 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2240)
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee apfApplyWlanPolicy: Apply WLAN Policy over PMIPv6 Client Mobility Type
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee override from intf group to an intf for roamed client, removing intf group from mscb
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee Applying Interface policy on Mobile, role Unassociated. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 192
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee Re-applying interface policy for client
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee 0.0.0.0 START (0) Changing IPv4 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2219)
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee 0.0.0.0 START (0) Changing IPv6 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2240)
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee 0.0.0.0 START (0) Initializing policy
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee 0.0.0.0 START (0) Change state to AUTHCHECK (2) last state START (0)
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee 0.0.0.0 AUTHCHECK (2) Change state to L2AUTHCOMPLETE (4) last state AUTHCHECK (2)
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee 0.0.0.0 L2AUTHCOMPLETE (4) Change state to DHCP_REQD (7) last state L2AUTHCOMPLETE (4)
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee Resetting web IPv4 acl from 255 to 255
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee Resetting web IPv4 Flex acl from 65535 to 65535
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee Stopping deletion of Mobile Station: (callerId: 53)
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee 0.0.0.0 DHCP_REQD (7) State Update from Mobility-Incomplete to Mobility-Complete, mobility role=ExpAnchor, client state=APF_MS_STATE_ASSOCIATED
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee 0.0.0.0 DHCP_REQD (7) Change state to DHCP_REQD (7) last state DHCP_REQD (7)
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee 0.0.0.0 DHCP_REQD (7) pemAdvanceState2 5761, Adding TMP rule
*mmListen: Nov 07 10:05:04.764: 54:26:96:3e:4b:ee 0.0.0.0 DHCP_REQD (7) Adding Fast Path rule
type = Airespace AP - Learn IP address
on AP 00:00:00:00:00:00, slot 0, interface = 13, QOS = 0
IPv4 ACL ID = 255, IP
*mmListen: Nov 07 10:05:04.765: 54:26:96:3e:4b:ee 0.0.0.0 DHCP_REQD (7) Fast Path rule (contd...) 802.1P = 0, DSCP = 0, TokenID = 15206 Local Bridging Vlan = 192, Local Bridging intf id = 13
*mmListen: Nov 07 10:05:04.765: 54:26:96:3e:4b:ee 0.0.0.0 DHCP_REQD (7) Successfully plumbed mobile rule (IPv4 ACL ID 255, IPv6 ACL ID 255, L2 ACL ID 255)
*pemReceiveTask: Nov 07 10:05:04.767: 54:26:96:3e:4b:ee Set bi-dir guest tunnel for 54:26:96:3e:4b:ee as in Export Anchor role
*pemReceiveTask: Nov 07 10:05:04.767: 54:26:96:3e:4b:ee 0.0.0.0 Added NPU entry of type 9, dtlFlags 0x4
*pemReceiveTask: Nov 07 10:05:04.767: 54:26:96:3e:4b:ee Sent an XID frame
*DHCP Socket Task: Nov 07 10:05:06.583: 54:26:96:3e:4b:ee DHCP received op BOOTREQUEST (1) (len 308,vlan 80, port 13, encap 0xec05)
*DHCP Socket Task: Nov 07 10:05:06.583: 54:26:96:3e:4b:ee DHCP (encap type 0xec05) mstype 3ff:ff:ff:ff:ff:ff
*DHCP Socket Task: Nov 07 10:05:06.583: 54:26:96:3e:4b:ee DHCP selecting relay 1 - control block settings:
dhcpServer: 0.0.0.0, dhcpNetmask: 0.0.0.0,
dhcpGateway: 0.0.0.0, dhcpRelay: 0.0.0.0 VLAN: 0
*DHCP Socket Task: Nov 07 10:05:06.583: 54:26:96:3e:4b:ee DHCP selected relay 1 - 192.168.80.1 (local address 192.168.99.1, gateway 192.168.99.254, VLAN 192, port 13)
*DHCP Socket Task: Nov 07 10:05:06.583: 54:26:96:3e:4b:ee DHCP transmitting DHCP REQUEST (3)
*DHCP Socket Task: Nov 07 10:05:06.583: 54:26:96:3e:4b:ee DHCP op: BOOTREQUEST, htype: Ethernet, hlen: 6, hops: 1
*DHCP Socket Task: Nov 07 10:05:06.583: 54:26:96:3e:4b:ee DHCP xid: 0x761692a1 (1981190817), secs: 5, flags: 0
*DHCP Socket Task: Nov 07 10:05:06.583: 54:26:96:3e:4b:ee DHCP chaddr: 54:26:96:3e:4b:ee
*DHCP Socket Task: Nov 07 10:05:06.583: 54:26:96:3e:4b:ee DHCP ciaddr: 0.0.0.0, yiaddr: 0.0.0.0
*DHCP Socket Task: Nov 07 10:05:06.583: 54:26:96:3e:4b:ee DHCP siaddr: 0.0.0.0, giaddr: 192.168.99.1
*DHCP Socket Task: Nov 07 10:05:06.583: 54:26:96:3e:4b:ee DHCP requested ip: 192.168.99.5
*DHCP Socket Task: Nov 07 10:05:06.583: 54:26:96:3e:4b:ee DHCP selecting relay 2 - control block settings:
dhcpServer: 0.0.0.0, dhcpNetmask: 0.0.0.0,
dhcpGateway: 0.0.0.0, dhcpRelay: 192.168.99.1 VLAN: 192
*DHCP Socket Task: Nov 07 10:05:06.583: 54:26:96:3e:4b:ee DHCP selected relay 2 - NONE (server address 0.0.0.0,local address 0.0.0.0, gateway 192.168.99.254, VLAN 192, port 13)
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee DHCP received op BOOTREPLY (2) (len 572,vlan 0, port 0, encap 0x0)
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee DHCP setting server from ACK (server 192.168.80.1, yiaddr 192.168.99.5)
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee Static IP client associated to interface guest which can support client subnet.
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee 192.168.99.5 DHCP_REQD (7) Change state to WEBAUTH_REQD (8) last state DHCP_REQD (7)
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee 192.168.99.5 WEBAUTH_REQD (8) pemAdvanceState2 6671, Adding TMP rule
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee 192.168.99.5 WEBAUTH_REQD (8) Replacing Fast Path rule
type = Airespace AP Client - ACL passthru
on AP 00:00:00:00:00:00, slot 0, interface = 13, QOS = 0
IPv4 ACL
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee 192.168.99.5 WEBAUTH_REQD (8) Fast Path rule (contd...) 802.1P = 0, DSCP = 0, TokenID = 15206 Local Bridging Vlan = 192, Local Bridging intf id = 13
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee 192.168.99.5 WEBAUTH_REQD (8) Successfully plumbed mobile rule (IPv4 ACL ID 255, IPv6 ACL ID 255, L2 ACL ID 255)
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee Plumbing web-auth redirect rule due to user logout
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee Assigning Address 192.168.99.5 to mobile
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee DHCP success event for client. Clearing dhcp failure count for interface guest.
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee DHCP success event for client. Clearing dhcp failure count for interface guest.
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee DHCP transmitting DHCP ACK (5)
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee DHCP op: BOOTREPLY, htype: Ethernet, hlen: 6, hops: 0
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee DHCP xid: 0x761692a1 (1981190817), secs: 0, flags: 0
*DHCP Proxy Task: Nov 07 10:05:06.586: 54:26:96:3e:4b:ee DHCP chaddr: 54:26:96:3e:4b:ee
*DHCP Proxy Task: Nov 07 10:05:06.587: 54:26:96:3e:4b:ee DHCP ciaddr: 0.0.0.0, yiaddr: 192.168.99.5
*DHCP Proxy Task: Nov 07 10:05:06.587: 54:26:96:3e:4b:ee DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0
*DHCP Proxy Task: Nov 07 10:05:06.587: 54:26:96:3e:4b:ee DHCP server id: 1.1.1.1 rcvd server id: 192.168.80.1
*pemReceiveTask: Nov 07 10:05:06.589: 54:26:96:3e:4b:ee Set bi-dir guest tunnel for 54:26:96:3e:4b:ee as in Export Anchor role
*pemReceiveTask: Nov 07 10:05:06.589: 54:26:96:3e:4b:ee 192.168.99.5 Added NPU entry of type 2, dtlFlags 0x4
*pemReceiveTask: Nov 07 10:05:06.589: 54:26:96:3e:4b:ee Sent an XID frame
*ewmwebWebauth1: Nov 07 10:05:32.617: 54:26:96:3e:4b:ee Username entry (ttest) created for mobile, length = 5
*ewmwebWebauth1: Nov 07 10:05:32.617: 54:26:96:3e:4b:ee Username entry (ttest) created in mscb for mobile, length = 5
*ewmwebWebauth1: Nov 07 10:05:32.618: 54:26:96:3e:4b:ee 192.168.99.5 WEBAUTH_REQD (8) Change state to WEBAUTH_NOL3SEC (14) last state WEBAUTH_REQD (8)
*ewmwebWebauth1: Nov 07 10:05:32.618: 54:26:96:3e:4b:ee apfMsRunStateInc
*ewmwebWebauth1: Nov 07 10:05:32.618: 54:26:96:3e:4b:ee 192.168.99.5 WEBAUTH_NOL3SEC (14) Change state to RUN (20) last state WEBAUTH_NOL3SEC (14)
*ewmwebWebauth1: Nov 07 10:05:32.618: 54:26:96:3e:4b:ee Session Timeout is 0 - not starting session timer for the mobile
*ewmwebWebauth1: Nov 07 10:05:32.618: 54:26:96:3e:4b:ee 192.168.99.5 RUN (20) Reached PLUMBFASTPATH: from line 6559
*ewmwebWebauth1: Nov 07 10:05:32.618: 54:26:96:3e:4b:ee 192.168.99.5 RUN (20) Replacing Fast Path rule
type = Airespace AP Client
on AP 00:00:00:00:00:00, slot 0, interface = 13, QOS = 0
IPv4 ACL ID = 255, IPv6 ACL ID
*ewmwebWebauth1: Nov 07 10:05:32.618: 54:26:96:3e:4b:ee 192.168.99.5 RUN (20) Fast Path rule (contd...) 802.1P = 0, DSCP = 0, TokenID = 15206 Local Bridging Vlan = 192, Local Bridging intf id = 13
*ewmwebWebauth1: Nov 07 10:05:32.618: 54:26:96:3e:4b:ee 192.168.99.5 RUN (20) Successfully plumbed mobile rule (IPv4 ACL ID 255, IPv6 ACL ID 255, L2 ACL ID 255)
*pemReceiveTask: Nov 07 10:05:32.626: 54:26:96:3e:4b:ee Set bi-dir guest tunnel for 54:26:96:3e:4b:ee as in Export Anchor role
*pemReceiveTask: Nov 07 10:05:32.626: 54:26:96:3e:4b:ee 192.168.99.5 Added NPU entry of type 1, dtlFlags 0x4
*pemReceiveTask: Nov 07 10:05:32.627: 54:26:96:3e:4b:ee Sending a gratuitous ARP for 192.168.99.5, VLAN Id 192
Here are the complete logs from WLC2 CLI:
(WLC2) >debug client 54:26:96:3e:4b:ee
(WLC2) >*pemReceiveTask: Nov 07 10:00:16.787: 54:26:96:3e:4b:ee 0.0.0.0 Removed NPU entry.
*apfMsConnTask_0: Nov 07 10:04:31.368: 54:26:96:3e:4b:ee Adding mobile on LWAPP AP 00:22:bd:98:3a:30(1)
*apfMsConnTask_0: Nov 07 10:04:31.368: 54:26:96:3e:4b:ee Association received from mobile on AP 00:22:bd:98:3a:30
*apfMsConnTask_0: Nov 07 10:04:31.368: 54:26:96:3e:4b:ee 0.0.0.0 START (0) Changing ACL 'none' (ACL ID 0) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:1633)
*apfMsConnTask_0: Nov 07 10:04:31.368: 54:26:96:3e:4b:ee Applying site-specific IPv6 override for station 54:26:96:3e:4b:ee - vapId 4, site 'default-group', interface 'management'
*apfMsConnTask_0: Nov 07 10:04:31.368: 54:26:96:3e:4b:ee Applying IPv6 Interface Policy for station 54:26:96:3e:4b:ee - vlan 80, interface id 0, interface 'management'
*apfMsConnTask_0: Nov 07 10:04:31.368: 54:26:96:3e:4b:ee STA - rates (8): 140 18 152 36 176 72 96 108 0 0 0 0 0 0 0 0
*apfMsConnTask_0: Nov 07 10:04:31.368: 54:26:96:3e:4b:ee 0.0.0.0 START (0) Initializing policy
*apfMsConnTask_0: Nov 07 10:04:31.368: 54:26:96:3e:4b:ee 0.0.0.0 START (0) Change state to AUTHCHECK (2) last state AUTHCHECK (2)
*apfMsConnTask_0: Nov 07 10:04:31.368: 54:26:96:3e:4b:ee 0.0.0.0 AUTHCHECK (2) Change state to L2AUTHCOMPLETE (4) last state L2AUTHCOMPLETE (4)
*apfMsConnTask_0: Nov 07 10:04:31.368: 54:26:96:3e:4b:ee 0.0.0.0 L2AUTHCOMPLETE (4) DHCP Not required on AP 00:22:bd:98:3a:30 vapId 4 apVapId 4for this client
*apfMsConnTask_0: Nov 07 10:04:31.369: 54:26:96:3e:4b:ee Not Using WMM Compliance code qosCap 00
*apfMsConnTask_0: Nov 07 10:04:31.369: 54:26:96:3e:4b:ee 0.0.0.0 L2AUTHCOMPLETE (4) Plumbed mobile LWAPP rule on AP 00:22:bd:98:3a:30 vapId 4 apVapId 4
*apfMsConnTask_0: Nov 07 10:04:31.369: 54:26:96:3e:4b:ee 0.0.0.0 L2AUTHCOMPLETE (4) Change state to DHCP_REQD (7) last state DHCP_REQD (7)
*apfMsConnTask_0: Nov 07 10:04:31.369: 54:26:96:3e:4b:ee apfMsAssoStateInc
*apfMsConnTask_0: Nov 07 10:04:31.369: 54:26:96:3e:4b:ee apfPemAddUser2 (apf_policy.c:223) Changing state for mobile 54:26:96:3e:4b:ee on AP 00:22:bd:98:3a:30 from Idle to Associated
*apfMsConnTask_0: Nov 07 10:04:31.369: 54:26:96:3e:4b:ee Stopping deletion of Mobile Station: (callerId: 48)
*apfMsConnTask_0: Nov 07 10:04:31.369: 54:26:96:3e:4b:ee Sending Assoc Response to station on BSSID 00:22:bd:98:3a:30 (status 0) ApVapId 4 Slot 1
*apfMsConnTask_0: Nov 07 10:04:31.369: 54:26:96:3e:4b:ee apfProcessAssocReq (apf_80211.c:5276) Changing state for mobile 54:26:96:3e:4b:ee on AP 00:22:bd:98:3a:30 from Associated to Associated
*DHCP Socket Task: Nov 07 10:04:31.722: 54:26:96:3e:4b:ee DHCP received op BOOTREQUEST (1) (len 308,vlan 80, port 1, encap 0xec03)
*DHCP Socket Task: Nov 07 10:04:31.723: 54:26:96:3e:4b:ee DHCP dropping packet due to ongoing mobility handshake exchange, (siaddr 0.0.0.0, mobility state = 'apfMsMmQueryRequested'
*DHCP Socket Task: Nov 07 10:04:33.461: 54:26:96:3e:4b:ee DHCP received op BOOTREQUEST (1) (len 308,vlan 80, port 1, encap 0xec03)
*DHCP Socket Task: Nov 07 10:04:33.461: 54:26:96:3e:4b:ee DHCP dropping packet due to ongoing mobility handshake exchange, (siaddr 0.0.0.0, mobility state = 'apfMsMmQueryRequested'
*apfReceiveTask: Nov 07 10:04:34.238: 54:26:96:3e:4b:ee 0.0.0.0 DHCP_REQD (7) State Update from Mobility-Incomplete to Mobility-Complete, mobility role=ExpForeign, client state=APF_MS_STATE_ASSOCIATED
*apfReceiveTask: Nov 07 10:04:34.238: 54:26:96:3e:4b:ee apfMsRunStateInc
*apfReceiveTask: Nov 07 10:04:34.238: 54:26:96:3e:4b:ee 0.0.0.0 DHCP_REQD (7) Change state to RUN (20) last state RUN (20)
*apfReceiveTask: Nov 07 10:04:34.240: 54:26:96:3e:4b:ee 0.0.0.0 RUN (20) Reached PLUMBFASTPATH: from line 4563
*apfReceiveTask: Nov 07 10:04:34.240: 54:26:96:3e:4b:ee 0.0.0.0 RUN (20) Adding Fast Path rule
type = Airespace AP Client
on AP 00:22:bd:98:3a:30, slot 1, interface = 1, QOS = 0
ACL Id = 255, Jumbo Frames = NO
*apfReceiveTask: Nov 07 10:04:34.240: 54:26:96:3e:4b:ee 0.0.0.0 RUN (20) Fast Path rule (contd...) 802.1P = 0, DSCP = 0, TokenID = 1506 IPv6 Vlan = 80, IPv6 intf id = 0
*apfReceiveTask: Nov 07 10:04:34.240: 54:26:96:3e:4b:ee 0.0.0.0 RUN (20) Successfully plumbed mobile rule (ACL ID 255)
*pemReceiveTask: Nov 07 10:04:34.243: 54:26:96:3e:4b:ee Set bi-dir guest tunnel for 54:26:96:3e:4b:ee as in Export Foreign role
*pemReceiveTask: Nov 07 10:04:34.256: 54:26:96:3e:4b:ee 0.0.0.0 Added NPU entry of type 1, dtlFlags 0x4
*DHCP Socket Task: Nov 07 10:04:36.055: 54:26:96:3e:4b:ee DHCP received op BOOTREQUEST (1) (len 308,vlan 80, port 1, encap 0xec03)
*DHCP Socket Task: Nov 07 10:04:36.055: 54:26:96:3e:4b:ee DHCP processing DHCP REQUEST (3)
*DHCP Socket Task: Nov 07 10:04:36.055: 54:26:96:3e:4b:ee DHCP op: BOOTREQUEST, htype: Ethernet, hlen: 6, hops: 0
*DHCP Socket Task: Nov 07 10:04:36.055: 54:26:96:3e:4b:ee DHCP xid: 0x761692a1 (1981190817), secs: 1280, flags: 0
*DHCP Socket Task: Nov 07 10:04:36.055: 54:26:96:3e:4b:ee DHCP chaddr: 54:26:96:3e:4b:ee
*DHCP Socket Task: Nov 07 10:04:36.055: 54:26:96:3e:4b:ee DHCP ciaddr: 0.0.0.0, yiaddr: 0.0.0.0
*DHCP Socket Task: Nov 07 10:04:36.056: 54:26:96:3e:4b:ee DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0
*DHCP Socket Task: Nov 07 10:04:36.056: 54:26:96:3e:4b:ee DHCP requested ip: 192.168.99.5
*DHCP Socket Task: Nov 07 10:04:36.056: 54:26:96:3e:4b:ee DHCP successfully bridged packet to EoIP tunnel
*DHCP Socket Task: Nov 07 10:04:36.060: 54:26:96:3e:4b:ee DHCP received op BOOTREPLY (2) (len 312,vlan 80, port 1, encap 0xec05)
*DHCP Socket Task: Nov 07 10:04:36.060: 54:26:96:3e:4b:ee DHCP processing DHCP ACK (5)
*DHCP Socket Task: Nov 07 10:04:36.060: 54:26:96:3e:4b:ee DHCP op: BOOTREPLY, htype: Ethernet, hlen: 6, hops: 0
*DHCP Socket Task: Nov 07 10:04:36.061: 54:26:96:3e:4b:ee DHCP xid: 0x761692a1 (1981190817), secs: 0, flags: 0
*DHCP Socket Task: Nov 07 10:04:36.061: 54:26:96:3e:4b:ee DHCP chaddr: 54:26:96:3e:4b:ee
*DHCP Socket Task: Nov 07 10:04:36.061: 54:26:96:3e:4b:ee DHCP ciaddr: 0.0.0.0, yiaddr: 192.168.99.5
*DHCP Socket Task: Nov 07 10:04:36.061: 54:26:96:3e:4b:ee DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0
*DHCP Socket Task: Nov 07 10:04:36.061: 54:26:96:3e:4b:ee DHCP server id: 1.1.1.1 rcvd server id: 1.1.1.1
*DHCP Socket Task: Nov 07 10:04:36.062: 54:26:96:3e:4b:ee 192.168.99.5 RUN (20) DHCP Address Re-established
*DHCP Socket Task: Nov 07 10:04:36.062: 54:26:96:3e:4b:ee Assigning Address 192.168.99.5 to mobile
*DHCP Socket Task: Nov 07 10:04:36.062: 54:26:96:3e:4b:ee DHCP success event for client. Clearing dhcp failure count for interface management.