In this post we will learn/test how the dynamic VLAN assignment works.
Basic Info:
Dynamic VLAN assignment: It pushes a wireless user into a specific VLAN based on his identity. This task of assigning users to a specific VLAN is handled by a RADIUS authentication server (i.e. ACS).
It’s a type of identity networking. It allows us to have single SSID, but allows specific users to use different VLAN attributes based on the user credentials.
This task of assigning users to a specific VLAN is handled by a RADIUS authentication server (ACS 5.2 in my case). This can be used, for example, to allow the wireless host to remain on the same VLAN as it moves within a campus network.
As a result, when a client attempts to associate to a LAP registered with a controller, the LAP passes the credentials of the user to the RADIUS server for validation. Once the authentication is successful, the RADIUS server passes (IETF) attributes to the user. These RADIUS attributes decide the VLAN ID that should be assigned to the wireless client.
***In my post I am using a single SSID
My Topology:
Let’s take an Example:
- We will create a SSID “XYZ” and assign a non-routed VLAN (99) or management VLAN to it.
- Now we have Groups of employees in our company “Production, Admin and Sales”.
- VLANs as per Roles.(Production – 13, Admin – 14, Sales – 17 )
Steps to Configuration:
- Configure WLC
- Configure ACS server
- Verification
Configure WLC
We must configure the WLC so it can communicate with the RADIUS server in order to authenticate the clients.
- Configure ACS on WLC:
From the controller GUI, click Security> Authentication
- Create dynamic interface (for VLAN 13, 14 and 17)
Example for VLAN 13, same we have to do for VLAN 14 & 17
Controller GUI, in the Controller > Interfaces
- Create a WLAN and assign to a Non Routed VLAN or management interface
From the controller GUI, go to WLANs > Create New
My WLAN is “XYZ”
Enable AAA override feature:
CLI Command to enable: config wlan aaa-override enable wlan-id
Configure ACS (RADIUS) Server
- Configure Network Resources.
AAA Client (WLC management IP), Location, and device type
- Configure User and Identity Store
Create Identity Group, Users and then assign users to Identity Groups(Production, Admin and Sales Users)
Create Identity Store Sequence
- Define policy elements.
Custom Profile
End Station Filter
Create Authorization Profiles
- Apply access policies.
Select EAP Method
Assign Auth. Profile as per identity
- Configure Network Resources.
First we will add the WLC as an AAA client on the RADIUS server so that the WLC can pass the user credentials to the RADIUS server.
Create a Location type:
From the ACS GUI, go to Network Resources > Network Device Groups > Location, and click Create
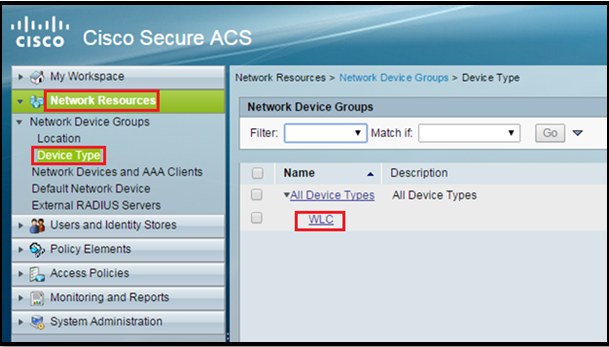
Crete Device Type:
Go to Network Resources > Network Device Groups > Device Type > Create
Add WLC as AAA client in ACS sever:
Go to Network Resources > Network Devices and AAA Clients. Put the WLC IP and shared secret (it must be same as in WLC)
- Configure User and Identity Store
Create Identity Group, Users and then assign users to Identity Groups:
In this post we will create three types of users (Production, Admin and Sales Users)
For Identity Groups:
Go to Users and Identity Stores > Identity Groups > Create
For Users:
Go to Users and Identity Stores > Internal Identity Stores > Users > Create
Create Identity Store Sequence:
As we don’t need it in this post (only internal user option will also work)
Go to Users and Identity Stores > Identity Stores Sequences > Create
- Define policy elements.
Custom Profile
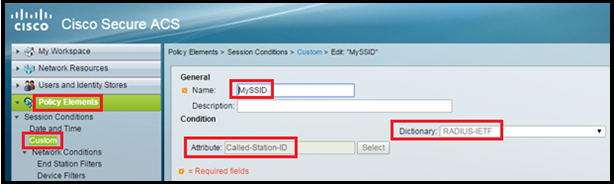
Create a Custom SSID Profile or create an END STATION filter (we will use only one method from this and that will be CUSTOM SSID)
Go to Policy Elements > Custom> Create
Enter the Name (MySSID), choose Dictionary as RADIUS-IETF and Attribute as Called-Station-ID.
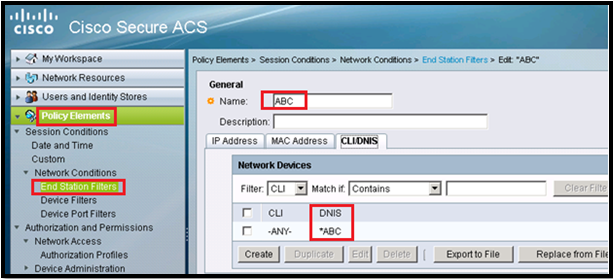
End Station Filter:
Go to Policy Elements> Network Conditions>End Station Filter>Create
*** We will not use this in this post
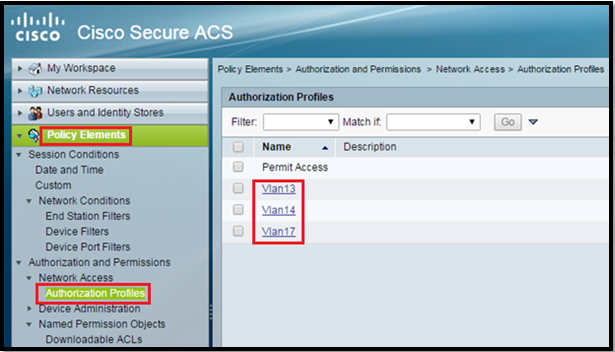
Create Authorization Profiles:
Go to Policy Elements > Authorization and Permissions > Network Access > Authorization Profiles > Create.
IN this post we are using vlan 13, 14 and 17 so we need three Auth Profiles.
Two ways to do: Either under Common Tasks or under RADIUS Attributes:
Both ways are shown here.
So in end auth profile will look like this:
- Access Policies
We are using Radius Authentication we have to use Default Network Access.
Select which EAP method we would like the wireless Clients to Authenticate. In this post we will use EAP-FAST or PEAP.
Select Identity under Default Network Access as “MyLab” which we created earlier.
Configure Authorization Rules:
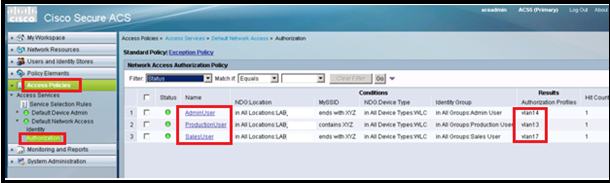
Go to Access Policies > Access Services > Default Network Access > Authorization.
We can customize under what conditions we will allow user access to the network and what authorization profile (attributes) we will pass once authenticated. In this post, we selected Location, SSID, Device Type, and Identity Group.
Verification
Production User must go in vlan 13.
Sales User must go in vlan 17.
Admin User must go in vlan 14.
Thats all 🙂