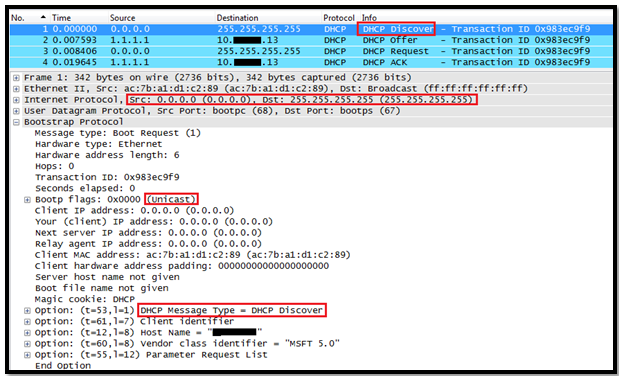
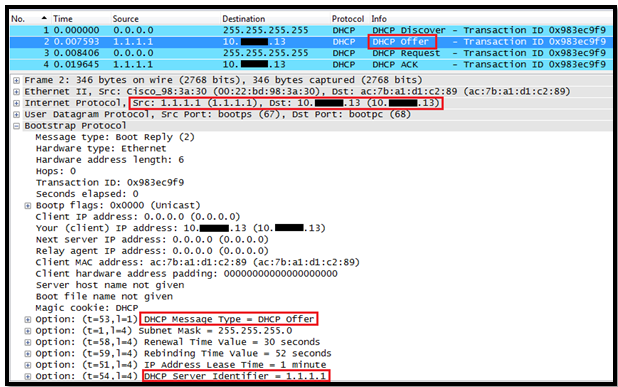
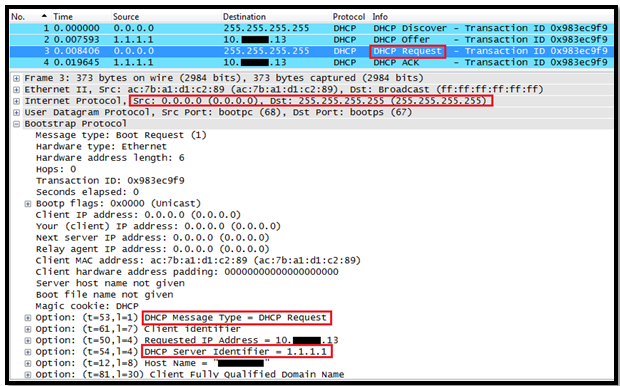
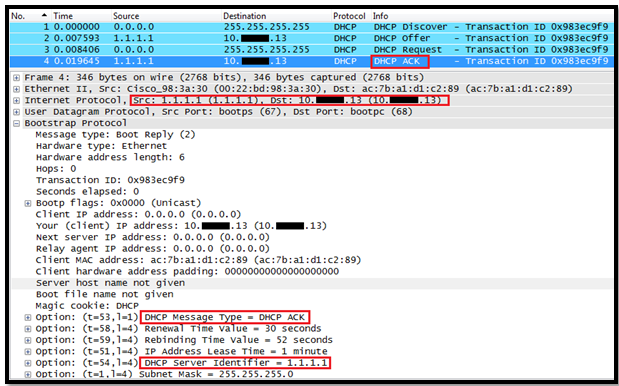
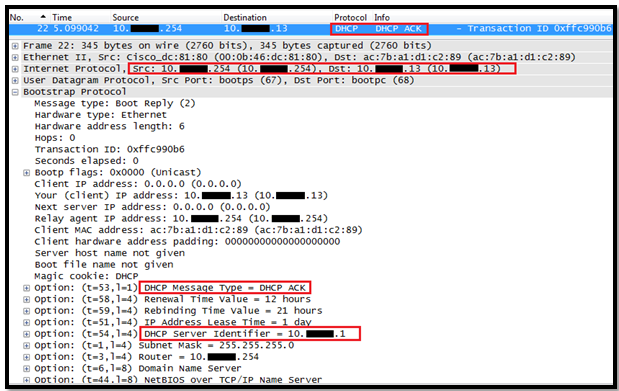
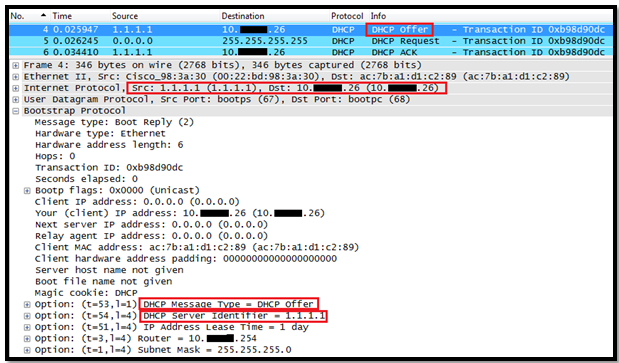
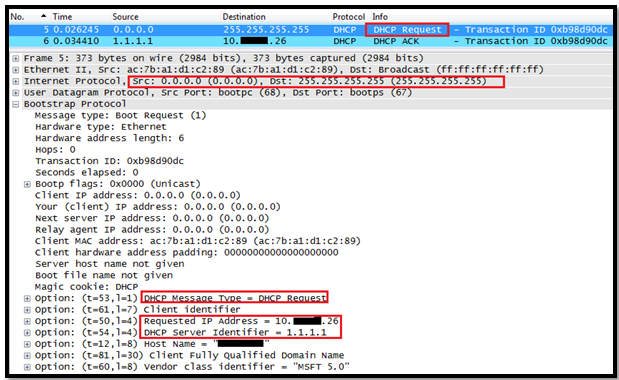
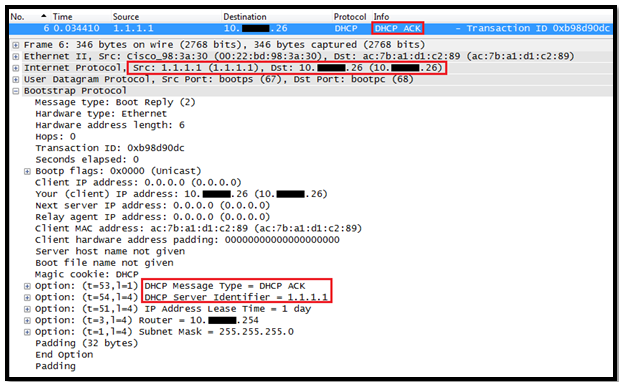
In this post we will see how the Layer 3 Roaming( inter subnet controller) roaming works on Controller.
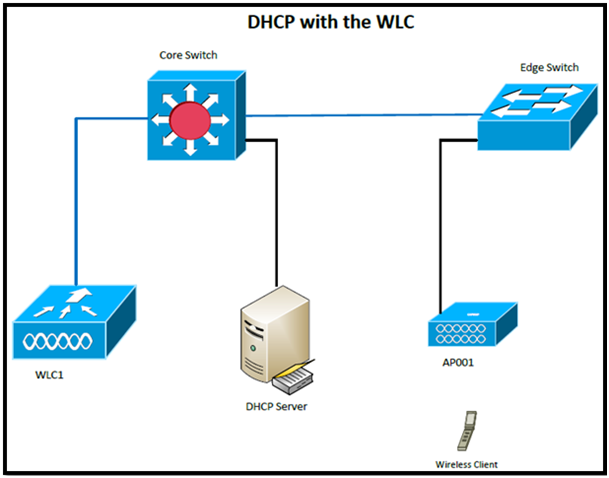
Here is my topology:

WLC1: 10.99.80.1, AP001 is connected to it
WLC2: 10.99.82.1, AP002 is connected to it.
If the client roams between APs registered to different controllers and the client WLAN on the two controllers is on different subnets, then an inter-subnet roam, or Layer 3 mobility event, takes place. For example, if a client is on WLAN-X on Controller-1 using VLANx and the client roams to WLAN-X on Controller-2, but WLAN-X on controller-2 is using VLANy, then an inter-subnet roam for that client occurs.
Inter-subnet roaming is similar to inter-controller roaming in that the controllers exchange mobility messages on the client roam. However, instead of moving the client database entry to the new controller, the original controller marks the client with an “Anchor” entry in its own client database. The database entry is copied to the new controller client database and marked with a “Foreign” entry in the new controller. The roam remains transparent to the wireless client, and the client maintains its original IP address.
In inter-subnet roaming, WLANs on both anchor and foreign controllers need to have the same network access privileges and no source-based routing or source-based firewalls in place. Otherwise, the clients may have network connectivity issues after the handoff.
Or
When the client roams between them, the controllers still exchange mobility messages, but they handle the client database entry in a completely different manner. The original controller marks the client entry as Anchor, whereas the new controller marks the client entry as Foreign. The two controllers are now referred to as anchor and foreign, respectively. The client has no knowledge of this and retains its original IP address on the new controller. Traffic flow to and from the client on the network becomes asymmetrical. Traffic from the client is bridged directly to the wired network by the foreign controller. The foreign controller spoofs the IP and MAC address of the client. Traffic from the wired network to the client, however, is received by the original controller and sent to the new controller through an Ethernet over IP (EtherIP) tunnel to the new controller. The new controller then passes that traffic to the client.
If the client roams back to the original controller, the Anchor and Foreign markings are removed and the client database entry is deleted from the foreign controller. If the client should roam to a different foreign controller, the original anchor controller is maintained, and the foreign client entry is transferred to the new foreign controller.
First my client is already connected to AP001.
See the summary:
(WLC1) >show client summary
Number of Clients................................ 1
MAC Address AP Name Status WLAN Auth Protocol Port Wired
----------------- ----------------- ------------- -------------- ---- ---------------- ---- -----
ab:26:96:3e:4b:ee AP001 Associated 8 Yes 802.11a 1 N/A
(WLC1) >show client detail ab:26:96:3e:4b:ee
Client MAC Address............................... ab:26:96:3e:4b:ee
Client Username ................................. N/A
AP MAC Address................................... ab:22:bd:98:3a:30
AP Name.......................................... AP001
Client State..................................... Associated
Client NAC OOB State............................. Access
Wireless LAN Id.................................. 8
BSSID............................................ 00:22:bd:98:3a:38
Connected For ................................... 22 secs
Channel.......................................... 36
IP Address....................................... 10.99.81.40
Association Id................................... 1
Authentication Algorithm......................... Open System
Reason Code...................................... 1
Status Code...................................... 0
Session Timeout.................................. 0
Client CCX version............................... No CCX support
QoS Level........................................ Silver
802.1P Priority Tag.............................. disabled
WMM Support...................................... Enabled
Power Save....................................... OFF
Supported Rates.................................. 6.0,9.0,12.0,18.0,24.0,36.0,48.0,54.0
Mobility State................................... Local
Mobility Move Count.............................. 0
Security Policy Completed........................ Yes
Policy Manager State............................. RUN
Policy Manager Rule Created...................... Yes
ACL Name......................................... none
ACL Applied Status............................... Unavailable
Policy Type...................................... WPA2
Authentication Key Management.................... PSK
Encryption Cipher................................ CCMP (AES)
Management Frame Protection...................... No
EAP Type......................................... Unknown
Interface........................................ intanchor
VLAN............................................. 81
Quarantine VLAN.................................. 0
Access VLAN...................................... 81
Client Capabilities:
.
.
.
(WLC1) >
Now to remove the client form WLC1, I will reset the AP001 because we want to see if client can roam to AP002 or not with keeping the same IP.
*** But make sure that WLC must have Anchor-Foreign setup.

So now our client moved to AP002.
***It is important to remember that a Layer 3 mobility event occurs only when the interface assigned to the WLAN between the controllers is not the same. Whether or not the management interfaces of each controller are in the same subnet has no bearing on a client Layer 3 roaming event.
In a Layer 3 roaming scenario, traffic returning to the wireless client goes through the anchor WLC. The anchor WLC establishes an Ethernet-over-IP (EoIP) tunnel to forward client traffic to the foreign WLC where it is then delivered to the client. All traffic originated by the client is forwarded out the corresponding VLAN interface to which the WLAN is mapped to at foreign WLC. The client’s original IP address and default gateway IP (MAC) address remain the same. All traffic, other than that which is destined for the local subnet, is forwarded to the default router where the foreign WLC substitutes the client’s default gateway MAC address with the MAC address of the default gateway associated with dynamic interface/VLAN at the foreign controller.
The following occurs when a client roams across a Layer 3 boundary:
- The client begins with a connection to AP001 on WLC 1.
- This creates an ANCHORentry in WLC 1’s client database.
- As the client moves away from AP001 and begins association with AP002, WLC 2 sends a mobility announcement to its peers in the mobility group looking for the WLC with information for the client MAC address.
- WLC 1 responds to the announcement, handshakes, and ACKs.
- The client database entry for the roaming client is copied to WLC 2, and marked as FOREIGN.
- A simple key exchange is made between the client and AP, the client is added to WLC 2’s database, which is similar to the anchor controller’s entry, except that the client entry is marked as FOREIGN.
- Data being sent to the WLAN client is now EoIP tunneled from the anchor WLC to the foreign WLC.
- Data sent by the WLAN client is sent out a local interface VLAN at the foreign controller.
***It is important to remember that a Layer 3 mobility event occurs only when the interface assigned to the WLAN between the controllers is not the same. Whether or not the management interfaces of each controller are in the same subnet has no bearing on a client Layer 3 roaming event
Once client moved, we see entry in WLC1 & marked as “Anchor”
(WLC1) >show client summary
Number of Clients................................ 1
MAC Address AP Name Status WLAN Auth Protocol Port Wired
----------------- ----------------- ------------- -------------- ---- ---------------- ---- -----
ab:26:96:3e:4b:ee 10.99.82.1 Associated 8 Yes Mobile 1 N/A
(WLC1) >show client detail ab:26:96:3e:4b:ee
Client MAC Address............................... ab:26:96:3e:4b:ee
Client Username ................................. N/A
AP MAC Address................................... 00:00:00:00:00:00
AP Name.......................................... N/A
Client State..................................... Associated
Client NAC OOB State............................. Access
Wireless LAN Id.................................. 8
BSSID............................................ 00:00:00:00:00:07
Connected For ................................... 140 secs
Channel.......................................... N/A
IP Address....................................... 10.99.81.40
Association Id................................... 0
Authentication Algorithm......................... Open System
Reason Code...................................... 1
Status Code...................................... 0
Session Timeout.................................. 0
Client CCX version............................... No CCX support
QoS Level........................................ Silver
802.1P Priority Tag.............................. disabled
WMM Support...................................... Enabled
Power Save....................................... OFF
Supported Rates.................................. 6.0,9.0,12.0,18.0,24.0,36.0,48.0,54.0
Mobility State................................... Anchor
Mobility Foreign IP Address...................... 10.99.82.1
Mobility Move Count.............................. 0
Security Policy Completed........................ Yes
Policy Manager State............................. RUN
Policy Manager Rule Created...................... Yes
ACL Name......................................... none
ACL Applied Status............................... Unavailable
Policy Type...................................... WPA2
Authentication Key Management.................... PSK
Encryption Cipher................................ CCMP (AES)
Management Frame Protection...................... No
EAP Type......................................... Unknown
Interface........................................ intanchor
VLAN............................................. 81
Quarantine VLAN.................................. 0
Access VLAN...................................... 81
Client Capabilities:
.
.
(WLC1) >
Check the client entry as Foreign on WLC2:
(WLC2) >show client summary
Number of Clients................................ 1
MAC Address AP Name Status WLAN Auth Protocol Port Wired
----------------- ----------------- ------------- -------------- ---- ---------------- ---- -----
ab:26:96:3e:4b:ee AP002 Associated 8 Yes 802.11g 1 N/A
(WLC2) >show client detail ab:26:96:3e:4b:ee
Client MAC Address............................... ab:26:96:3e:4b:ee
Client Username ................................. N/A
AP MAC Address................................... 00:3a:99:14:13:70
AP Name.......................................... AP002
Client State..................................... Associated
Client NAC OOB State............................. Access
Wireless LAN Id.................................. 8
BSSID............................................ 00:3a:99:14:13:77
Connected For ................................... 8 secs
Channel.......................................... 1
IP Address....................................... 10.99.81.40
Association Id................................... 1
Authentication Algorithm......................... Open System
Reason Code...................................... 1
Status Code...................................... 0
Session Timeout.................................. 0
Client CCX version............................... No CCX support
QoS Level........................................ Silver
802.1P Priority Tag.............................. disabled
WMM Support...................................... Enabled
Power Save....................................... OFF
Supported Rates.................................. 1.0,2.0,5.5,11.0,6.0,9.0,12.0,18.0,24.0,36.0,48.0,54.0
Mobility State................................... Foreign
Mobility Anchor IP Address....................... 10.99.80.1
Mobility Move Count.............................. 1
Security Policy Completed........................ Yes
Policy Manager State............................. RUN
Policy Manager Rule Created...................... Yes
ACL Name......................................... none
ACL Applied Status............................... Unavailable
Policy Type...................................... WPA2
Authentication Key Management.................... PSK
Encryption Cipher................................ CCMP (AES)
Management Frame Protection...................... No
EAP Type......................................... Unknown
Interface........................................ intforeign
VLAN............................................. 84
Quarantine VLAN.................................. 0
Access VLAN...................................... 81
Client Capabilities:
.
.
(WLC2) >
Basic Workflow for Inter Subnet Roaming:


Asymmetric Tunneling
To know more about handoff we must see the logs from both WLC:
Handoff logs from WLC1:
(WLC1) > debug mobility handoff enable
(WLC1) >*mmListen: Jul 09 09:21:21.315: ab:26:96:3e:4b:ee Mobility packet received from:
*mmListen: Jul 09 09:21:21.315: ab:26:96:3e:4b:ee 10.99.82.1, port 16666
*mmListen: Jul 09 09:21:21.316: ab:26:96:3e:4b:ee type: 3(MobileAnnounce) subtype: 0 version: 1 xid: 25 seq: 101 len 116 flags 0
*mmListen: Jul 09 09:21:21.316: ab:26:96:3e:4b:ee group id: d7f8a4f2 cb038b78 641818bb a26869b4
*mmListen: Jul 09 09:21:21.316: ab:26:96:3e:4b:ee mobile MAC: ab:26:96:3e:4b:ee, IP: 0.0.0.0, instance: 0
*mmListen: Jul 09 09:21:21.316: ab:26:96:3e:4b:ee VLAN IP: 10.99.84.3, netmask: 255.255.255.0
*mmListen: Jul 09 09:21:21.316: Switch IP: 10.99.82.1
*mmListen: Jul 09 09:21:21.316: Vlan List payload not found, ignoring ...
*mmListen: Jul 09 09:21:21.316: IP Address don't compare for client ab:26:96:3e:4b:ee is 0
*mmListen: Jul 09 09:21:21.316: ab:26:96:3e:4b:ee Handoff as Local, Client IP: 10.99.81.40 Anchor IP: 10.99.80.1
*mmListen: Jul 09 09:21:21.316: Anchor Mac : 00.21.d8.fa.66.00
*mmListen: Jul 09 09:21:21.316: ab:26:96:3e:4b:ee Mobility packet sent to:
*mmListen: Jul 09 09:21:21.316: ab:26:96:3e:4b:ee 10.99.82.1, port 16666
*mmListen: Jul 09 09:21:21.316: ab:26:96:3e:4b:ee type: 5(MobileHandoff) subtype: 0 version: 1 xid: 25 seq: 132 len 546 flags 0
*mmListen: Jul 09 09:21:21.316: ab:26:96:3e:4b:ee group id: d7f8a4f2 cb038b78 641818bb a26869b4
*mmListen: Jul 09 09:21:21.316: ab:26:96:3e:4b:ee mobile MAC: ab:26:96:3e:4b:ee, IP: 10.99.81.40, instance: 0
*mmListen: Jul 09 09:21:21.316: ab:26:96:3e:4b:ee VLAN IP: 10.99.81.1, netmask: 255.255.255.0
*apfReceiveTask: Jul 09 09:21:21.316: ab:26:96:3e:4b:ee 10.99.81.40 RUN (20) mobility role update request from Local to Anchor Peer = 10.99.82.1, Old Anchor = 10.99.80.1, New Anchor = 10.99.80.1
*apfReceiveTask: Jul 09 09:21:21.318: ab:26:96:3e:4b:ee 10.99.81.40 RUN (20) Plumbing duplex mobility tunnel to 10.99.82.1 as Anchor (VLAN 81)
*apfReceiveTask: Jul 09 09:21:21.318: ab:26:96:3e:4b:ee Mobility Response: IP 10.99.81.40 code Handoff Indication (2), reason Client handoff successful - anchor released (1), PEM State RUN, Role Anchor(2)
Handoff logs from WLC2:
(WLC2) >debug mobility handoff enable
(WLC2) >*Dot1x_NW_MsgTask_0: Jul 09 09:39:02.572: ab:26:96:3e:4b:ee Mobility query, PEM State: L2AUTHCOMPLETE
*Dot1x_NW_MsgTask_0: Jul 09 09:39:02.573: ab:26:96:3e:4b:ee Mobility packet sent to:
*Dot1x_NW_MsgTask_0: Jul 09 09:39:02.573: ab:26:96:3e:4b:ee 10.99.80.1, port 16666
*Dot1x_NW_MsgTask_0: Jul 09 09:39:02.573: ab:26:96:3e:4b:ee type: 3(MobileAnnounce) subtype: 0 version: 1 xid: 22 seq: 89 len 116 flags 0
*Dot1x_NW_MsgTask_0: Jul 09 09:39:02.573: ab:26:96:3e:4b:ee group id: d7f8a4f2 cb038b78 641818bb a26869b4
*Dot1x_NW_MsgTask_0: Jul 09 09:39:02.573: ab:26:96:3e:4b:ee mobile MAC: ab:26:96:3e:4b:ee, IP: 0.0.0.0, instance: 0
*Dot1x_NW_MsgTask_0: Jul 09 09:39:02.574: ab:26:96:3e:4b:ee VLAN IP: 10.99.84.3, netmask: 255.255.255.0
*mmListen: Jul 09 09:39:02.575: ab:26:96:3e:4b:ee Mobility packet received from:
*mmListen: Jul 09 09:39:02.575: ab:26:96:3e:4b:ee 10.99.80.1, port 16666
*mmListen: Jul 09 09:39:02.575: ab:26:96:3e:4b:ee type: 5(MobileHandoff) subtype: 0 version: 1 xid: 22 seq: 118 len 546 flags 0
*mmListen: Jul 09 09:39:02.575: ab:26:96:3e:4b:ee group id: d7f8a4f2 cb038b78 641818bb a26869b4
*mmListen: Jul 09 09:39:02.575: ab:26:96:3e:4b:ee mobile MAC: ab:26:96:3e:4b:ee, IP: 10.99.81.40, instance: 0
*mmListen: Jul 09 09:39:02.575: ab:26:96:3e:4b:ee VLAN IP: 10.99.81.1, netmask: 255.255.255.0
*mmListen: Jul 09 09:39:02.575: Switch IP: 10.99.80.1
*mmListen: Jul 09 09:39:02.575: Mobility handoff, NAC State Payload [ Client's NAC OOB State : Access, Quarantine VLAN :0, Access VLAN : 81 ]
*mmListen: Jul 09 09:39:02.575: ab:26:96:3e:4b:ee Mobility handoff for client:Ip: 10.99.81.40 Anchor IP: 10.99.80.1, Peer IP: 10.99.80.1
*apfReceiveTask: Jul 09 09:39:02.579: ab:26:96:3e:4b:ee Handoff confirm: Pre Handoff PEM State: RUN
*apfReceiveTask: Jul 09 09:39:02.579: ab:26:96:3e:4b:ee Pem State update: RUN(20), VAP Security mask 40004000, IPsec len: 0, ACL Name: ''
*apfReceiveTask: Jul 09 09:39:02.581: ab:26:96:3e:4b:ee 10.99.81.40 RUN (20) mobility role update request from Unassociated to Foreign Peer = 10.99.80.1, Old Anchor = 10.99.80.1, New Anchor = 10.99.80.1
*apfReceiveTask: Jul 09 09:39:02.583: ab:26:96:3e:4b:ee 10.99.81.40 RUN (20) Plumbing duplex mobility tunnel to 10.99.80.1 as Foreign, (VLAN 84)
*apfReceiveTask: Jul 09 09:39:02.583: ab:26:96:3e:4b:ee Configured Anchor for mobile ab:26:96:3e:4b:ee. Sending Igmp query
*apfReceiveTask: Jul 09 09:39:02.583: ab:26:96:3e:4b:ee Mobility Response: IP 10.99.81.40 code Handoff (1), reason Handoff success (0), PEM State RUN, Role Foreign(3)
*bcastReceiveTask: Jul 09 09:39:02.598: Sending IGMP query First Time to 00:3a:99:14:13:70 ap for mgid 5
*bcastReceiveTask: Jul 09 09:39:02.598: Entry for ap 00:3a:99:14:13:70, IGMP query packet not queued for mgid 5... Enquing the Query packet...
*bcastReceiveTask: Jul 09 09:39:03.456: Sending IGMP query to 00:3a:99:14:13:70 ap for mgid 5, Query count: 2
*bcastReceiveTask: Jul 09 09:39:04.456: Sending IGMP query to 00:3a:99:14:13:70 ap for mgid 5, Query count: 1