In this post we will see how to configure a Wireless LAN Controller (WLC) and Cisco ISE Server (Cisco Identity Service Engine) so that the AAA server can authenticate management users on the controller. We will also see that how different management users can receive different privileges using Vendor-specific Attributes (VSAs) returned from the Cisco ISE RADIUS server.
Parameters:
ISE Server: 172.99.xx.1
WLC: 172.99.80.1 (TestWLC1)
Shared Secret: CISCO123456789
Read/Write User: sandeeprw, Password: Testwlc1rw
Read/Only User: sandeepro, Password: Testwlc1ro
Now we need to configure WLC and ISE so that:
- Any user who login to the WLC with the username as sandeeprw is given full administrative access to the WLC.
- Any user who login to the WLC with the username as sandeepro is given read-only access to the WLC.
Step1: Cisco WLC Configuration
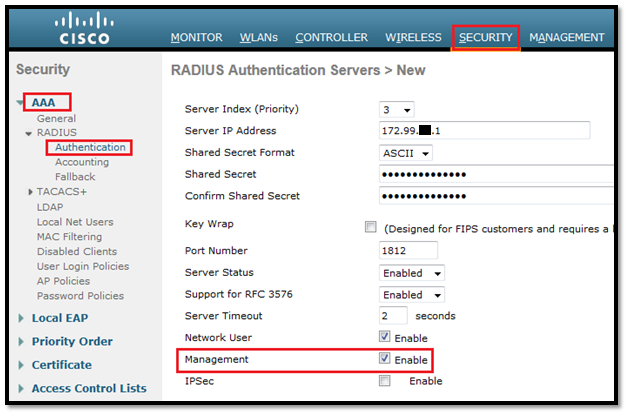
- Login to WLC GUI, click Security > AAA > RADIUS > Authentication > New. The RADIUS Authentication server page appears. Click on New to add a server and then enter all the detail.
- Check the Management radio button in order to allow the RADIUS Server to authenticate users who login to the WLC.
Note: Make sure that the shared secret configured on this WLC will also be the same shared secret on the RADIUS server. Only then the WLC can communicate with the RADIUS server.
- Verify whether the WLC is configured to be managed by Cisco ISE. In order to do this, click Security > AAA > RADIUS>Authentication from the WLC GUI.
- We can see that the Management check box is enabled for RADIUS server 172.99.xx.1. This illustrates that ISE is allowed to authenticate the management users on the WLC.
Step2: Cisco ISE configuration
1) Add the WLC as an AAA client to the RADIUS server.
2) Create User Identity Groups for users.
3) Configure a user with read-write access and assign to specific User Identity Group.
4) Configure a user with read-only access and assign to specific User Identity Group.
5) Create Authorization profile and assign Diff. RADIUS IETF attributes for these users.
6) Create Authentication / Authorization policy for these internal users.
Add the WLC as an AAA Client to the RADIUS Server
Login to ISE the click on Administration > Network Devices > Add then enter the details of WLC and don’t forget to enter same shared secret as we did in WLC.
And clicks save.
Create User Identity Groups for users.
To create user identity groups, click on Administration > Identity Management > Groups > User identity Groups > Add then enter the Name and description.
Configure a user with read-write access and assign to specific User Identity Group.
RW: username-sandeeprw, password: Testwlc1rw
Click on Administration > Identity Management > Identities > User > Add then enter the details and assign this user to WLC-AdminRW group, save it.
Configure a user with read-only access and assign to specific User Identity Group.
RO: username- sandeepro, password: Testwlc123ro
Click on Administration > Identity Management > Identities > User > Add then enter the details and assign this user to WLC-AdminRO group, save it.
Create Authorization Profile and assign diff. Radius attributes for these users.
To authenticate a user via RADIUS server, for controller login and management, we must add the user to the RADIUS database with the IETF RADIUS attribute Service-Type set to the appropriate value according to the user’s privileges.
- In order to set read-write privileges for the user, set the Service-Type Attribute to Administrative.
- In order to set read-only privileges for the user, set the Service-Type Attribute to NAS-Prompt.
Login to ISE GUI then go to Policy > Policy Elements > Results
Create Authentication / Authorization policy for these internal users
To create Authentication policy: Login to ISE, click on Policy > Authentication.
Here is the full policy name:
AuthWLCAdmin: If {DEVICE:Device Type equals All Device Types#Wireless LAN Controller} {Allows Protocol: Default Network Access} Default: use Internal user
Authorization Policy:
Save to apply changes.
Step3: Verification
Now it’s time for testing
First with username: sandeeprw (read write access)
username: sandeepro (read only access)
Then I tried to create a WLAN with read-only access, the output was “Authorization Failed No sufficient privileges”
Hence Proved 🙂













Salutation, maybe this is not on theme but anyway, I have been reading about your site and it looks truly tidy. impassioned about your activity. I’m building a new blog and hard put to make it appear great, and provide really good content. I have revealed much on your site and I look forward to more updates and will be coming back.
Thank you for kind words 🙂