In this post we will learn how to provide or control WLC management user’s access via TACAS+ server.
We will create 3 users:
User1: Full Admin rights on WLC – sandeeprw
User2: Read-Only rights to WLC (Only allow one tab”WLAN” as admin access) – sandeepro
User3: Lobby user to create Guest Accounts – sandeeplobby
Parameters:
ACS Server: 192.168.205.5
WLC: 192.168.112.10
Shared Secret: Test12345
Read/Write User: sandeeprw, Password: sandeeprw
Read/Only User: sandeepro, Password: sandeepro
Lobby User: sandeeplobby, Password: sandeeplobby
Steps:
- Add ACS server to WLC as TACAS+ server
- Add WLC as AAA client to ACS.
- Create Identity Groups.
- Create Users and assign to respective Identity Groups
- Assign shell profiles to Users
- Configure Access Policies for specific Users
- Assign the Priority order for management access.
- Verification
So let’s start with configuration:
Add ACS server to WLC as TACAS+ server
Go to WLC GUI, click Security > AAA > TACAS+ > Authentication. Enter the parameters specific to the server. Also put Accounting& Authorization server info as well.
Add WLC as AAA client to ACS
Login to ACS and then go to Network Resources > Network Devices and AAA Clients
Must select TACAS+ check box and put the same shared secret as we did while adding ACS to WLC.
Create Identity Groups
Create Identity groups for different users.
These are the Groups:
Admin-Lobby
Admin-RO
Admin-RW
Create Users and assign to respective Identity Groups
Assign shell profiles to Users
Here we will create shell profile and assign the custom attributes to users.
Admin Users: role1 as ALL
Read-Only User: role1 as WLAN
Lobby Users: role1 as MONITOR
Configure Access Policies for specific Users
Create Authorization rules under default Network Access:
It will look like this:
Assign the Priority order for management access
Authentication Oder for management users on the WLC.
Security > Priority Order > Management User.
Verification
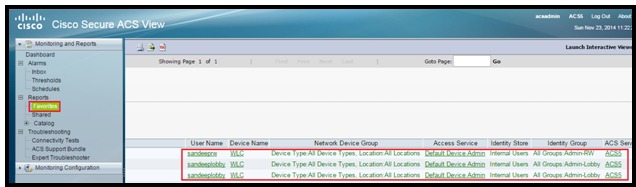
To verify each account, we must login with different users and check it.
Verification Logs from ACS about users attempts:
That’s all 🙂
In the next post we will learn the AAA override /Dynamic VLAN Assignment feature.